Source:
http://www.isf.rl.af.mil:8001/IRD/isisjitf/isis/amhs/isad/amhs4.html
Information Systems Accreditation Document
Volume 4 of 4
System Security Requirements
for the
Department of Defense Intelligence Information System (DoDIIS)
Automated Message Handling System (AMHS) V2.x
Approved by:
S. Hersch, MDA AMHS Program Mgr
Approved by:
LtCol J. Schepley
Electronics Systems Center
AMHS Program Manager
Approved by:
H. Williams, MDA AMHS QA Mgr
Approved by:
G. Gies, MDA AMHS Chief Engineer
Prepared by:
J. Evans, AMHS Development Mgr.
Submitted by:
McDonnell Douglas Aerospace (MDA)
8201 Greensboro Drive, McLean, VA, 22102
Developed for:
Electronic Systems Center (ESC)
Air Force Materiel Command (AFMC)
TABLE OF CONTENTS
1. Purpose
2. AMHS Architecture
3. Identification of Named Objects
4. Identification of AMHS Subjects
5. Assumptions
6. Access Controls 6
6.1 Information Labels
6.2 Discretionary Access Controls (DAC)
6.3 Mandatory Access Controls (MAC)
6.4 Release Marking Controls(RMAC)
7. Integrity
APPENDICES
A. Increment 1 AMHS Security Requirements
FIGURES
Figure 2-1 AMHS Context Diagram 2
Figure 3-1 Taxonomy of Mappings Between Named Objects
(AMHS Objects) and Files.
1.PURPOSE
The purpose of the Informal Security Policy Model (ISPM) is extracted from
Section 4 of Deborah J. Bodeau, Security Models in the System Design and
Development Process, March 1986, MITRE Working Paper WP 26652.
"There is a need for clear communications about security among the
organizations and individuals involved in developing and accrediting an
application system. An informal security model provides a possible means
of facilitating such communications. ...
"An informal model can facilitate communications about security in three
ways. First, an informal security model can be constructed early in system
development. Thus, it can provide a basis for discussions about specific
design issues. When an informal model is constructed early, it will be based
primarily on security policy and the general approach to system design, but
can incorporate information about COTS or other existing software that will
be part of the system. That is, it can mix generalities about the security
policy with specifics about the behavior of COTS software. ...
"Second, an informal model is written with the goal of providing
understanding of the security-relevant characteristics of the proposed system,
rather than providing a basis for proving theorems. Thus, it can be written
in natural language, supplemented by mathematical language and diagrams where
appropriate. This makes it accessible to a broader audience than a formal
model, which requires some degree of mathematical sophistication of its audience.
Since an informal model can be more widely read, it can provide the basis
for discussion and reasoning about the proposed system design. This discussion
can include representatives of the user, acquisition support organizations,
the contractor, and the DAA(s). Reasoning about the informal model includes
determining whether the system it describes enforces the security policy.
...
"Finally, an informal model can be adaptive: it can change over the course
of system development to incorporate changes in design, interpretations of
general policy statements, and details about specific system behavior as
they become available. As these details and changes are incorporated, the
resulting version of the informal model can be checked against the security
policy. ..."
Accordingly, this informal model provides a basis for discussing the
security-relevant characteristics of the DoDIIS AMHS in terms of the hardware
and software architecture, including the integrated COTS products that have
a bearing on security enforcement. It is presented in natural language at
an appropriate level of abstraction. Design and implementation details are
provided only to the extent that they enhance presentation and reasoning
about the security attributes of the AMHS.
2. AMHS Architecture
Figure 2-1 provides a context for discussing the AMHS and its environment.
The figure shows the site LAN which interconnects a number of user workstations
and intelligence application servers. The AMHS server is one of the intelligence
application servers on the site LAN.
The AMHS provides communications links for the site to external sources.
Specifically, the AMHS links to:
-
Communications Support Processor (CSP)
-
AGT Gateguard
-
Associated Press (AP)
-
United Press International (UPI)
-
Reuters
-
Foreign Broadcast Information Service (FBIS).
Formal AUTODIN messages arrive to and are sent from the site via the CSP.
This communication link is read/write. Formal message traffic can also be
received from the Local Digital Message Exchange (LDMX) network through the
AGT Gateguard front end system. The Gateguard supports a receive only capability.
Wire service traffic arrives over the AP, UPI, Reuters, and FBIS links. These
links are receive only.
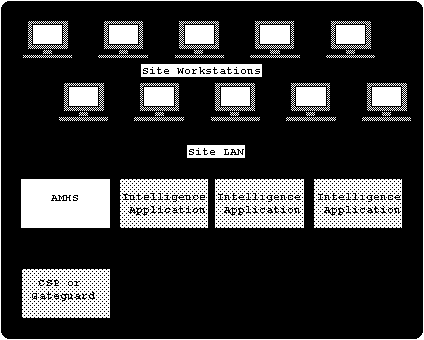
Figure 2-1, AMHS Context
Diagram
The AMHS is a distributed application that follows the client/server paradigm.
The server software resides on the AMHS server. (From the standpoint of this
model, the AMHS server is a single processor. However, its physical
implementation is on multiple processors (1-3) on the DEC 2100, the number
depending on the site size). The client software resides on the user
workstations.
Two COTS products are key to AMHS security and are considered in this informal
security policy model. The first is OSF/1, the operating system (OS) for
the AMHS server. OSF/1 provides protection features at the OS-level mandated
for compartmented mode systems. The AMHS design uses these OS-level protections
to provide necessary safeguards for the AMHS.
The second key COTS product is TOPIC. TOPIC is a text retrieval engine that
includes a system profiling mechanism. TOPIC system profiles are applied
as safeguards to enforce site discretionary access control policies for both
message distribution and retrospective search. The TOPIC software is distributed,
part executing on the AMHS server, and part executing as client software
on the user workstations.
3. Identification of Named Objects
THE AMHS SUPPORTS THREE NAMED OBJECTS. EACH OF THESE IS STORED AND MAINTAINED
ON THE AMHS SERVER.
|
Named Object
|
Description
|
Organization
|
|
|
Messages
|
Messages are ASCII text . They arrive via one of the communication links
(i.e., CSP, AP, AGT Gateguard, UPI, Reuters, and FBIS), or are created by
users for transmission to CSP and on to AUTODIN.
|
1 message per file.
|
|
|
|
|
Profiles
|
Profiles are implemented within TOPIC. They consist of "Profile TOPICs" (in
the form of concept trees) and "Profile Maps" (in the form of weights and
thresholds).
|
Many profiles per multiple files.
|
|
|
|
|
The AMHS supports three sets of profiles:
|
|
|
** System Profiles, used to enforce the site's Discretionary Access Control
Policy.
|
|
|
** Installed User Profiles, installed by the profile administrator and used
to determine profile-based message distribution.
|
|
|
** Uninstalled User Profiles, used for retrospective searches.
|
|
|
|
Message Queues
|
Message Queues are implemented within TOPIC (and are known within TOPIC as
"Hot Document Lists").
|
Many message queues per multiple files.
|
|
These objects are AMHS named objects. While AMHS V2.x no longer has CMW
requirements, compartmented mode design attributes have been retained in
the porting effort from the MLS+ system to the ported OSF/1 V2.x system.
Since CMW features have been retained in the AMHS, it is worth understanding
how the AMHS named objects map to CMW protected objects (i.e., files). The
mappings, however, do not affect the system high nature of AMHS V2.x.
Figure 3-1 presents, in matrix form, a taxonomy of the possible mappings.
The matrix also shows where each of the named objects fits into the taxonomy.
The matrix shows that Messages are "simple" named objects, with a straightforward
one-to-one mapping to CMW files. As a result, CMW security attributes such
as sensitivity labels, information labels, and read/write/execute bits are
automatically available for Messages.
The matrix further shows that Message Queues and Profiles
are complex objects, with a many-to-many mapping to CMW files. As a result,
CMW security attributes do not have a straightforward mapping to Message
Queues and Profiles.
4. Identification of AMHS Subjects
The AMHS supports two types of subjects: (1) users (and processes
acting on their behalf), and (2) processes operating independent of any user
(i.e. daemon processes). The AMHS supports five user roles:
In addition, one process acting on behalf of the user is
significant from the security perspective:
The AMHS supports a number of daemon processes, both on the
AMHS servers and the user workstations. With regards to system security,
the most significant daemon processes are:
|
|
|
AMHS Server Daemon Processes
|
|
*
|
Document Feed
|
The AMHS includes a Document Feed daemon for each external
communication link (i.e., CSP, AP, UPI, Reuters, and FBIS). Whenever a new
message arrives (on its communications link), Document Feed receives the
message, stores it on disk in the document database, and notifies the TOPIC
Partition Builder that a new message has arrived.
|
|
|
|
*
|
TOPIC Partition Builder
|
The TOPIC Partition Builder maintains certain indexes and
internal data structures for groups or "partitions" of messages. When notified
of a new message, it "adds" the message to the partition by updating its
indexes and internal data structures; it then notifies the TOPIC Server.
|
|
|
|
*
|
TOPIC Server
|
The TOPIC Server controls the flow of TOPIC processing. It
passes messages onto the TOPIC Profiler for profiling, fields requests from
TOPIC Clients, and schedules partition mergers.
|
|
|
|
*
|
TOPIC Profiler
|
The TOPIC Profiler compares messages against user and system
profiles. An entry is made in a user's Incoming Message Queue (TOPIC "Hot
Document List") whenever the message "hits" that user's profile, without
being excluded by the system profiles.
|
5. Assumptions
THE FOLLOWING ASSUMPTIONS ARE EXPLICITLY MADE ABOUT
THE AMHS ENVIRONMENT AND THE WAY IN WHICH THE AMHS IS USED:
6. ACCESS
CONTROLS
6.1 Information
Labels
Information labels are not required for the AMHS V2.x
system.
6.2 Discretionary Access Controls
(DAC)
The site's Discretionary Access Control policy applies to
profile-based distribution (of message traffic and free text) and retrospective
searches (of the message database). The site's DAC policy is captured in
the System Profiles (Assumption A5: Valid System Profiles).
DAC System Profiles: TOPIC supports System Profiles
through an entry called the "Access Profile" within the "User Preferences
File". During initialization, the TOPIC Client reads the User Preferences
File and then sets the System Profiles to the specified Access Profile. The
various system profiles, and their mappings to users (and User Preferences
Files), are managed by the Profile Administrator.
DAC Enforcement for Profile-Based Distribution:
Profile-based distribution is accomplished in a two step process. The TOPIC
Profiler performs the first step, applying user profiles to the incoming
stream of message traffic. The TOPIC Client performs the second step, applying
System Profiles to the results of the first step. In this way, profile-based
distribution is always subject to System Profiles and always complies with
the site's DAC policy.
DAC Enforcement for Retrospective Searches: Retrospective
searches are initiated by the user through the TOPIC Client. The user formulates
a search query via an (uninstalled) user profile. Before beginning the search,
the TOPIC Client logically "ands" the search query and the user's System
Profile, assuring that the search results are appropriately constrained.
Thus, retrospective searches always comply with the site's DAC policy.
6.3 Mandatory Access Controls
(MAC)
Mandatory Access Controls are not required for AMHS 2.x.
6.4 Release Marking Controls
(RMAC)
Release Marking Controls are not required for AMHS 2.x.
7. INTEGRITY
The AMHS similarly assures the integrity for outbound AUTODIN
messages during message composition, coordination, and release. The AMHS
calculates and stores a CRC-16 during message composition. If the message
composer changes any CRC-16 protected parts of the message, the AMHS recomputes
the CRC-16.
Coordinators do not receive messages, only a pointer to a
message that resides in the composer's or releaser's queues. In outbound
processing a CRC is done whenever the message is moved from one directory
to another.If the release authority changes any portion a message during
message release, the AMHS recomputes its CRC-16. After the final change and
CRC-16 recomputation, the release authority may release the message. The
AMHS then transmits the message along with its associated CRC-16 to the CSP
in order that message integrity may be verified by CSP.
CRC-16 is not used for AP, UPI, Reuters, or FBIS messages.
Appendix A
AMHS V2.x Security Requirements
|
1
|
AMHS capabilities specified for
users and/or user groups shall be available to any user of the AMHS including;
intelligence analysts, clerical staff, Message Administrator(s), System
Administrator(s), Profile Administrator(s), and Information System Security
Officer(s).
|
3.1.1
|
1
|
CSCI01
|
SM
|
|
|
|
2
|
AMHS shall be accreditable for the
System High mode of operation for the first increment.
|
3.1.4.1
|
1
|
CSCI01 HWCI01
|
AT FM GT IL IM MA MC NS OA OM PM
SC SM SY
|
Security
|
|
|
8
|
The AMHS shall ensure that access
to messages is granted only through the invocation of AMHS
functions.
|
3.1.4.4.1
|
1
|
CSCI01 HWCI01
|
AT FM GT IL IM MA MC NS OA OM PM
SC SM SY
|
Security
|
|
|
9
|
Access to storage objects shall
be controlled via the discretionary access control features of the AMHS.
|
3.1.4.4.1
|
1
|
CSCI01
|
AT FM GT IL IM MA MC NS OA OM PM
SC SM SY
|
Security
|
|
|
10
|
Each AMHS server shall collect and
forward audit information relevant to AMHS applications to the
CSE.
|
3.1.4.4.1
|
2
|
CSCI01
|
AT SM
|
Security Capability
|
|
|
11
|
The AMHS shall be able to audit
the following events: connection to the server, profile changes, System
Administrator/ISSO actions, message storage in workfiles, printout of messages
from server/workstation, the setting/modification of information labels by
users, and release functions.
|
3.1.4.4.1
|
1
|
CSCI01
|
AT IL IM OA OM PM SC SY
|
Security Capability
|
|
|
12
|
The AMHS shall provide audit trail
records in accordance with the requirements of the CSE.
|
3.1.4.4.1
|
2
|
CSCI01
|
AT
|
Security
|
|
|
92
|
The AMHS shall prohibit anyone,
other than the intended addressee or the designated alternate, from accessing
Eyes Only messages in any way, execpt for US/(approved country(ies)) Eyes
Only messages which are processed in the same manner as any other message
that does not contain special handling designators in accordance with the
requirements of sections 3.2.1.1.4 and 3.2.1.1.5.
|
3.2.1.1.3.2
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
95
|
The AMHS shall prohibit anyone other
than the intended addressee or the designated alternate, from accessing SPECAT
messages in any way.
|
3.2.1.1.3.3
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
97
|
For each message received, the AMHS
shall make an entry in the Message Queue of each action and information addressee
identified in the message header, provided that the addressee has a corresponding
entry in a table of local addresses as provided by the System
Administrator.
|
3.2.1.1.4
|
2
|
CSCI01
|
IM
|
Security Capability
|
|
|
102
|
The AMHS shall add these messages
to the Message Queues of each of the designated users, user groups and
organizations IAW the DAC features of the AMHS and the system profile
requirements of Sections 3.2.1.1.5 and 3.2.1.2.2.1.
|
3.2.1.1.4
|
2
|
CSCI01
|
IM
|
Security Capability
|
|
|
111
|
The AMHS shall provide the capability
to selectively prevent the dissemination of record messages to users based
on site specific discretionary access restrictions defined by the Profile
Administrator via system profiles.
|
3.2.1.1.5
|
1
|
CSCI01
IM
|
Security Capability
|
|
|
112
|
The discretionary access restrictions
defined in the system profiles shall have precedence over the dissemination
decisions based solely on user profiles.
|
3.2.1.1.5
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
136
|
The MDB shall have read-only permissions
for the header and text of all messages IAW the DAC features of
AMHS.
|
3.2.1.1.7
|
2
|
CSCI01
|
IM
|
Security Capability
|
|
|
223
|
Access to messages and to each of
the associated annotations (notes) shall be determined via the DAC features
of AMHS.
|
3.2.1.2.1.2
|
2
|
CSCI01
|
IM
|
Security Capability
|
|
|
228
|
The AMHS shall use system profiles
to selectively prevent the dissemination of record messages to users based
on site specific discretionary access restrictions defined by the Profile
Administrator.
|
3.2.1.2.2.1
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
242
|
The AMHS shall automatically apply
the selected system profiles or system profile modifications to each user
profile of each selected user, IAW the security requirements of Section
3.1.4.4.
|
3.2.1.2.2.1
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
278
|
Prior to executing each search of
the MDB requested by a user, the AMHS shall automatically apply any system
profiles associated with the user.
|
3.2.1.2.2.3
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
280
|
The AMHS shall prohibit access of
the system profiles (e.g., display, print) by users other than the Profile
Administrator.
|
3.2.1.2.2.3
|
1
|
CSCI01
|
PM
|
Security Capability
|
|
|
281
|
The AMHS shall ensure that only
the Profile Administrator has access to the system profiles (e.g., display
create, modify, print), including the system profiles that have been associated
with and applied to the user profiles of individual users other than the
Profile Administrator.
|
3.2.1.2.2.3
|
1
|
CSCI01
|
PM
|
Security Capability
|
|
|
309
|
Prior to executing a user's
retrospective search, the AMHS shall automatically apply any system profiles
associated with the user.
|
3.2.1.2.3
|
1
|
CSCI01
|
IM
|
Security Capability
|
|
|
311
|
The AMHS shall prohibit access to
the system profiles (e.g., display, print) by users other than the Profile
Administrator.
|
3.2.1.2.3
|
1
|
CSCI01
|
PM
|
Security Capability
|
|
|
322
|
The AMHS shall employ the CUBIC
program sixteen bit Cyclic Redundancy Check (CRC-16) to ensure the integrity
of each outbound AUTODIN message.
|
3.2.1.2.4
|
1
|
CSCI01
|
GT MC OM
|
Security Capability
|
|
|
339
|
Any change to the security information
in the message header by the release authority shall be audited by the
AMHS.
|
3.2.1.2.4
|
2
|
CSCI01
|
OM AT
|
Security Capability
|
|
|
473
|
The AMHS shall require positive
verification by the release authority of the security information in the
message header of a message to be released.
|
3.2.1.3.2
|
2
|
CSCI01
|
OM
|
Security Capability
|
|
|
475
|
Release of a message whose Information
Label is not within the AMHS's accreditation range shall be audited by the
AMHS.
|
3.2.1.3.2
|
2
|
CSCI01
|
AT OM
|
Security Capability
|
|
|
486
|
The AMHS shall also distribute copies
locally based on a comparison of the message content (header and text) with
user profiles and system profile requirements of Sections 3.2.1.1.5 and
3.2.1.2.2.1.
|
3.2.1.3.4
|
2
|
CSCI01
|
IM
|
Security Capability
|
|
|
513
|
The AMHS servers shall protect the
user account data against unauthorized access.
|
3.2.1.4.3
|
1
|
CSCI01
|
SC
|
Security Capability
|
|
|
633
|
Network programs shall be protected
from inadvertent modification.
|
3.2.3.1.1
|
2
|
CSCI01
|
SS
|
Security Capability
|
|
The following table contains data from the previous table
that was marked as "strikeout". Mosaic is unable to show this.
[End]
